See AI-powered security on full display at GSX 2025 | Sept 29 – Oct 1 Learn More >>
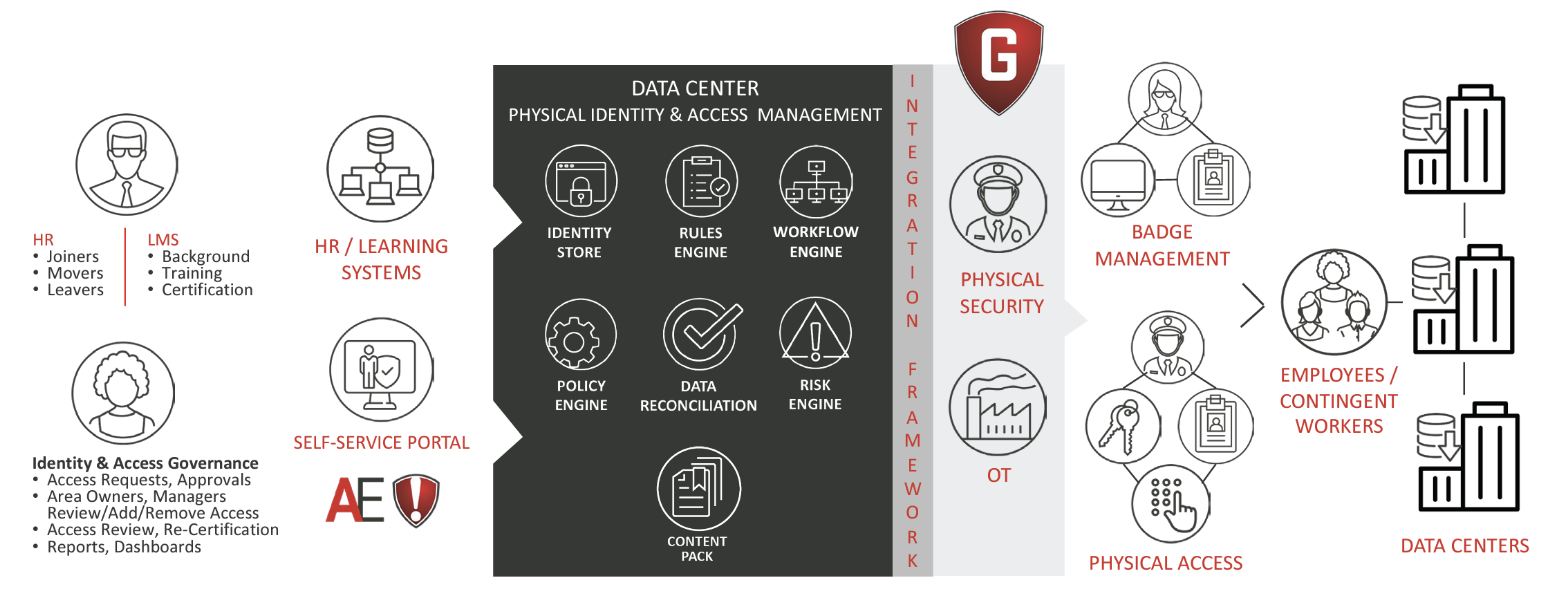
Data centers are the Crown Jewels of an enterprise. As companies digitally transform and global IP traffic surges, data centers have become the operational nerve center of an organization. It’s a critical infrastructure environment that needs to be highly protected—and requires a Three-Dimensional GRC (Governance Risk Compliance) and Security strategy that spans cyber/IT, Physical Security and OT disciplines.
Data centers are complex environments that house more than systems and technologies and as such also are part of a company’s cost center. If a server is damaged or part of a malicious threat or cyber takeover by an outsider, or insider, it could mean devastating loss to business continuity, company reputation and even ongoing profitability. Breaches or other data center compromises could also wreak drastic consequences on the business in the way of substantial regulatory fines or monetary damages.
Controlling who has access—and determining precisely how much—through full-service and automated identity, access and visitor management is a core component of effective data center Security. Organizations have different personnel, contractors, employees, visitors and even families and media entering the space. Everyone needs to be precisely tracked and accounted for in a history log that meets compliance and regulatory conformance requirements. When disparate systems and manual methods are used to provide identification and work notifications, the process becomes time consuming and error prone. This may also lead to credentials existing beyond the timeframe intended, posing additional potential Security risks and compromise.
Today’s data centers are operational nerve centers that need to be highly protected—and require a Three-Dimensional GRC (Governance Risk Compliance) and Security strategy that spans cyber/ IT, Physical Security and OT environments.
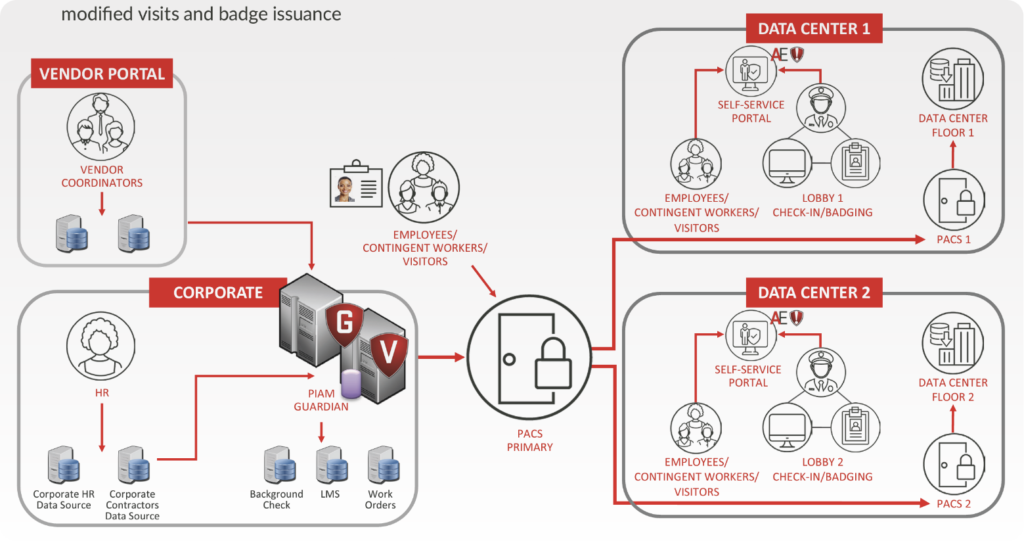
With the Alert Enterprise converged security platform, Data Center visits and temporary access can be configured to the length of time and type of work. Self-service portals for managers, area owners and contractors reduce the burden of support for security personnel. And real-time integration with HR/learning management systems and contractor databases further supports automated security policies and workflows.
According to the 2018 Cisco Annual Cybersecurity Report, nearly half of the Security risk organizations face stems from having multiple vendors and products.
Security convergence is the answer: integrated, automated and universal digital identities deployed across IT, Physical Security and OT systems. Three-Dimensional GRC and Security solutions identify and reduce risks, close security gaps and actively enforce rules, policies and processes across the entire enterprise.
Rather than rely on different systems and processes to submit, monitor and approve access, everything happens together with a converged solution— with all movement, access and egress logged and tracked.
Data center Security solutions need to seamlessly manage all categories of identities including employees, contractors, vendors and visitors. As well as a data and intelligence driven visitor management solution to track specifics on the entire population. With Alert Enterprise, businesses can apply a standard set of Security policies across all their data centers making sure all data is safe and company-wide operational integrity is maintained.
Visitor management software pre-integrated with Physical Access Control Systems (PACS) extends the same level of protection for visitors, enforcing request approval before granting access through the enterprise-class workflow engine. Add to the mix the fact that platforms are now integrated with AI-powered Identity Intelligence technology—and users can conduct risk analysis prior to provisioning access to help proactively protect against insider threats.
The Alert Enterprise platform allows data centers to automate and control exactly who has access to what critical assets. Benefits include:
The benefits of automated and converged badging and access solutions for data centers are clear:
Alert Enterprise delivers the following benefits and features to data centers and other vertical markets:
Just think: soon, you could be up and running with the latest security automation. Ready?