Something big is coming to ISC West Booth #13115

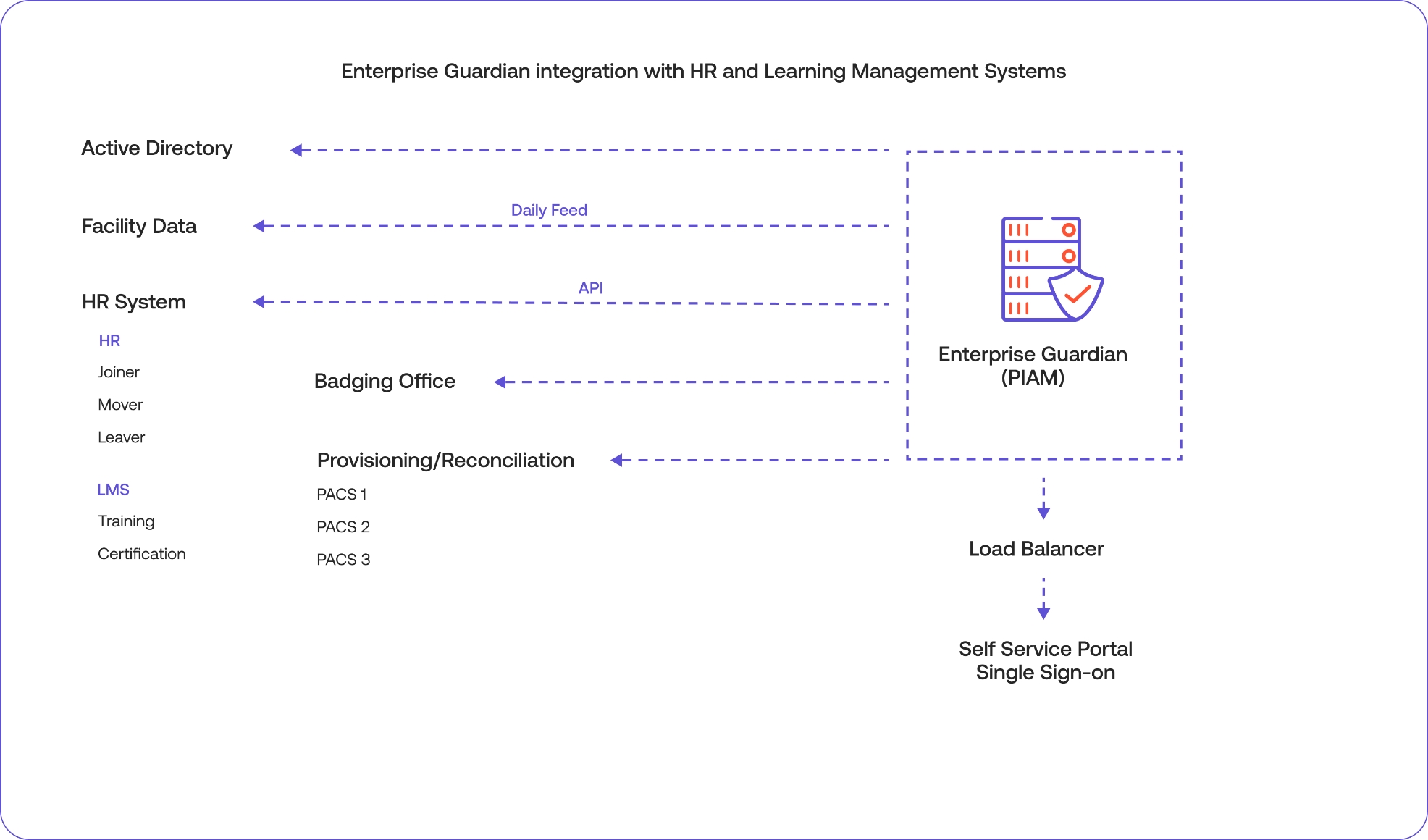
Immediate benefits arise from linking the most obviously siloed sources of identity information. Connecting the Human Resources Management System (HR) with the Physical Access Control Systems (PACS) delivers immediate integration value and allow managers to make timely, informed decisions about facility or corporate access requests based on job role, function and relevance.
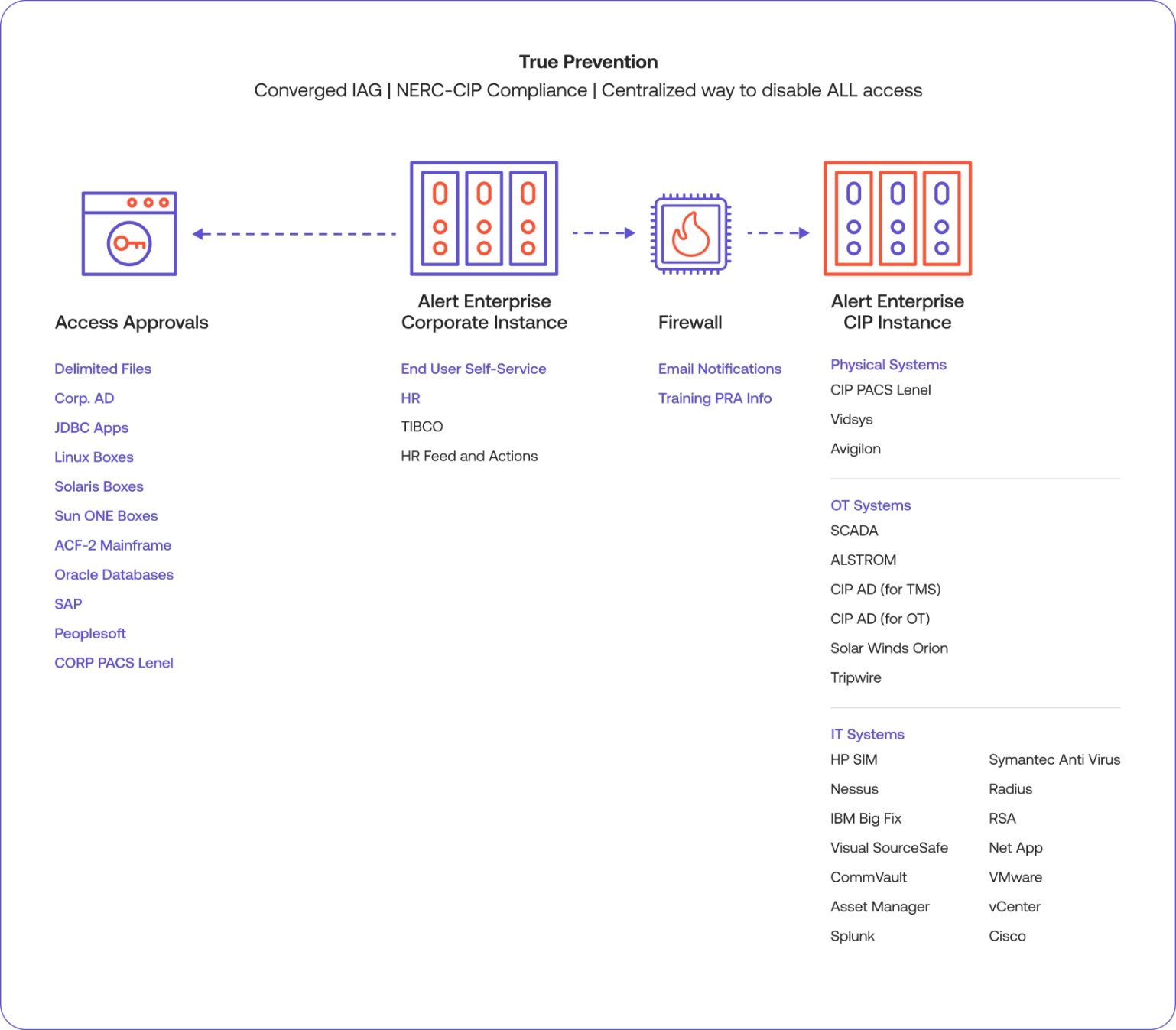
Another opportunity lies in linking PACS with IT directories that track who has access to corporate applications and resources such as the network, email, messaging, databases, etc. Some examples include LDAP – Lightweight Directory Access Protocol and AD – Active Directory.
Creating this critical connection delivers visibility into an individual’s role in the organization, their job function, the amount of facility access they need to get their job done as well as the amount of system or application access and authorization required to be productive while adhering to security policies.
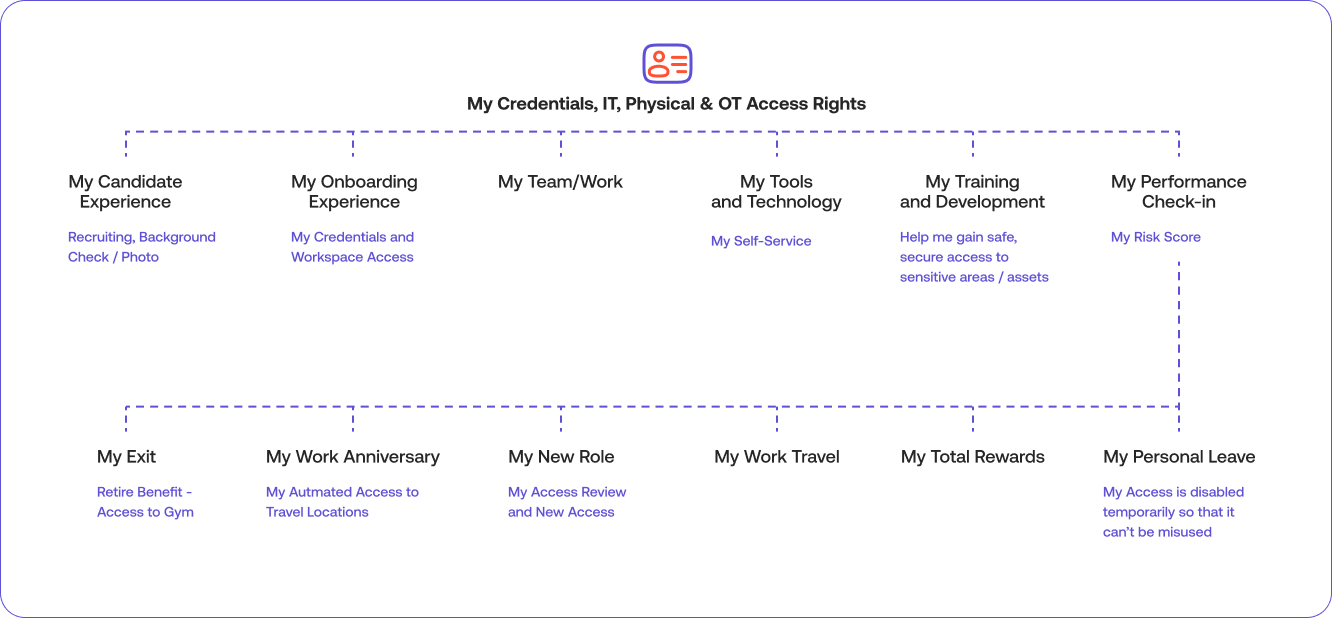
The combined categories of employees, contractors, vendors and visitors who have been granted access to the organization at any given point in time comprise the badged population. Security managers need to know how just how large this population is, what risks they pose to the enterprise and how to mitigate it. Incorporating risk scoring and behavior patterns into an identity profile allows for proactive risk analysis before granting or removing access.
SOC Insights & Response technology is powered by Generative AI and machine learning in combination with an active policy enforcement rules-based engine to reveal critical risk insights. For example, John Q is a control room worker who has been following a steady shift pattern of working 9-5, Monday through Friday. He suddenly starts showing up at midnight on a Saturday and uses his work badge to access a secure area. The deviation from the pattern of 9-5 on weekdays and the exception to the rules – that people with John’s role should not be accessing a room that stores critical assets – sets off an automated series of alerts to management stakeholders including security personnel.
The automatic baseline of identity profiles allows SOC Insights and Response software to quickly sort through millions of events to detect anomalies and trends for an effective response to potential malicious behavior and policy violations.
Enterprise Guardian software incorporates all four essential components of effective PIAM, allowing you to turn PIAM into a true business enabler.
Wherever you are in your PIAM journey, there’s no better time to step into the future of identity. Connect with our identity and security convergence experts to discuss your next steps.
At Alert Enterprise, trust is at the center of everything we do. We bring people, processes, data and technology together in true security convergence.
Subscribe to our newsletter:
Subscribe to our newsletter: